
Experience Endpoint Privilege Security Without the Risk
Take a guided product tour of CyberArk Endpoint Privilege Manager. See how you can enforce least privilege, stop credential theft, and protect endpoints across your enterprise.
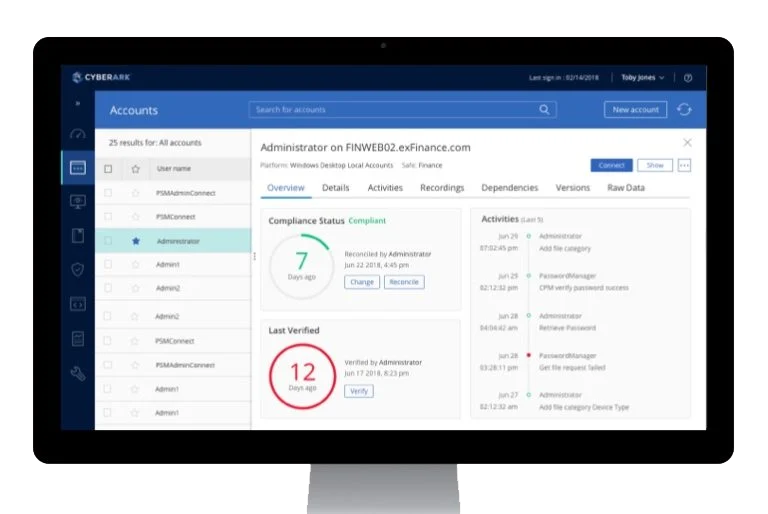
Control. Protect. Prove It.
Remove Admin Rights Safely
Eliminate local admin rights across Windows and macOS without disrupting workflows. Maintain user productivity by elevating only what’s required, when it’s needed. No re-imaging, no workarounds, no noise for the help desk.
Stop Credential Theft Fast
Prevent attackers from stealing and abusing cached credentials. Isolate privileged activity, enforce policy-based controls, and block lateral movement before it begins. No vault required at the endpoint.
Roll Out Without the Drag
Cloud-native and agent-based, EPM scales quickly across thousands of endpoints. Reduce deployment friction and accelerate time to value with automation, APIs, and built-in policy templates.
What to Expect
Your Guided Experience, Built for Real Security Outcome
01
Choose Your Journey
Select real-world use cases that match your environment.
02
Explore Key Features
Walk through core workflows including least privilege enforcement, credential protection, and policy creation.
03
See Value in Action
Learn how security and ops teams streamline access and stop attacks without user friction.
04
Map Next Steps
Get a no-pressure invite to speak with our team about rollout options and best practices.
Start Your PAM Tour

Why Alchemy?
Alchemy Technology Group is a CyberArk Premier Partner, trusted by leading enterprises to design, implement, and optimize identity security strategies. Our proven playbooks, certified engineers, and outcome-focused delivery ensure that your deployment achieves real results.